In 2025, the latest cyber threats targeting laptops in Kenya have skyrocketed—from ransomware locking your files, to phishing scams disguised as M-Pesa messages. Yet, many laptop users still rely on hope and luck instead of real protection. It’s like leaving your house unlocked in a crime-prone neighborhood and wondering why your TV’s gone.
Most people don’t act until they’ve already lost important files, passwords, or even cash. And by then, it’s too late. But here’s the good news: protecting your laptop doesn’t require expensive software or deep tech knowledge—just the right habits and tools.
This guide gives you a local, practical, no-fluff blueprint to secure your laptop from hackers, malware, ransomware, and snoops. Whether you’re a student, freelancer, business owner, or everyday user in Kenya—this is your wake-up call and your step-by-step survival kit.
Why Your Laptop Is a Prime Target in The Latest Cyber Threats In 2025
1. Cybercrime in Kenya Is Evolving—Fast In The Latest Cyber Threats
In early 2024, a Nairobi-based digital startup lost over KES 3 million after a ransomware attack encrypted all their client data. They had no offsite backups, and the attacker demanded payment in crypto. That’s not a global headline—that happened right here, and it wasn’t the only one.
From government portals like the Business Registration Service being hacked, eCitizen being hacked stopping various services from being implemented, scammers impersonating KRA agents and digital lenders, Kenya is no longer “too small” for cybercriminals. If anything, our growing digital economy makes us low-hanging fruit—especially for attacks designed to exploit common user behavior.
2. Remote Work + Public Wi-Fi = More Weak Points Fighting Latest Cyber Threats
With more Kenyans working from home or in coffee shops, unsecured public Wi-Fi has become a hacker’s playground. A recent test in Nairobi CBD found over 30 unsecured Wi-Fi networks—many of them being honeypots set up to spy on user traffic.
Even worse? Most users never log out of key apps like Gmail, Twitter, or M-Pesa.
3. AI is Making Attacks Smarter (and Harder to Detect) In Latest Cyber Threats
Tools like ChatGPT and WormGPT are being weaponized to craft perfect phishing emails—mimicking your bank, your boss, or even Safaricom. These attacks aren’t riddled with typos anymore. They’re clean, targeted, and personalized using data from your social media or leaked databases.
Real Example: A university student received an email claiming their HELB loan status had changed. The link led to a cloned portal that stole their login credentials—resulting in their personal info being leaked and sold.
4. Kenya’s Growing Digital Footprint = Bigger Bullseye In Latest Cyber Threats
With mobile money, digital IDs, and paperless businesses on the rise, laptops are the new wallets. They carry everything—from logins to bank info, ID copies, contracts, and more. That makes your laptop a more valuable target than ever.
Actionable Tip: Visit HaveIBeenPwned.com and enter your email to see if it’s been leaked. Many Kenyans are shocked to learn that their info is already floating around on the dark web.
Essential Laptop Security Tools Every Kenyan Should Use In Fighting The Latest Cyber Threats
Your laptop needs more than just antivirus—think of it as an ecosystem where every part plays a role in protection. Here’s your security toolkit, curated for Kenyan needs, budgets, and behavior patterns.
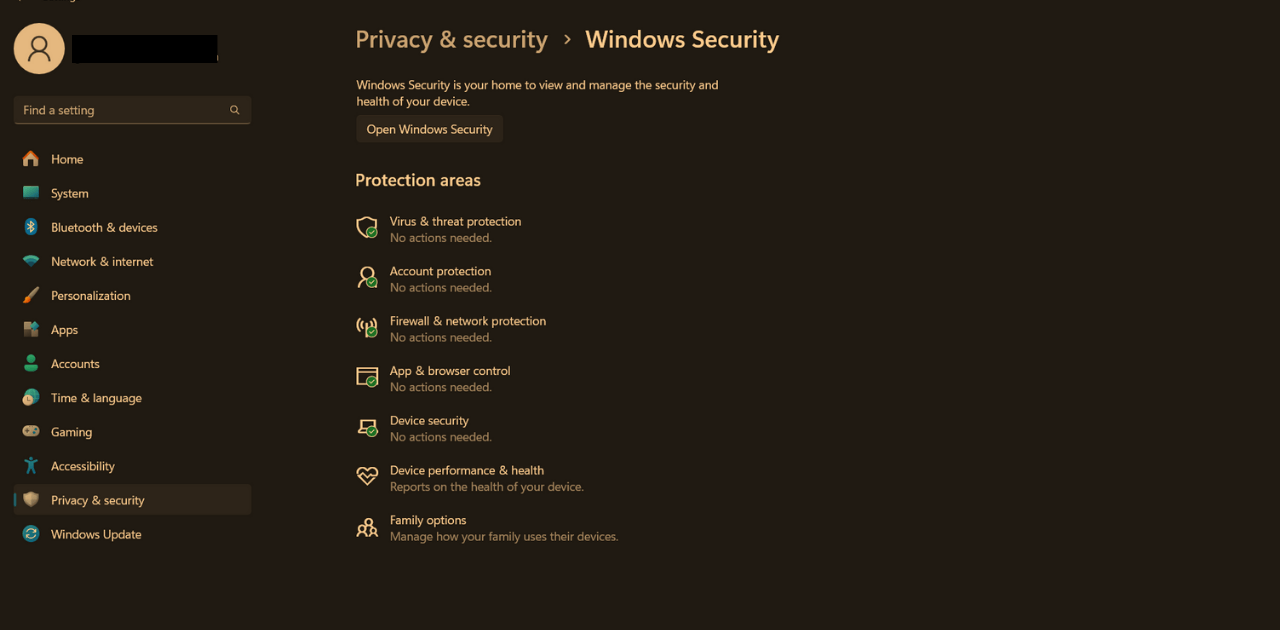
Enable Your Laptop Firewall and Use Network Protection Tools In Facing The Latest Cyber Threats
What Does a Firewall Actually Do Against The Latest Cyber Threats?
A firewall monitors incoming and outgoing traffic, blocking anything suspicious. It’s your first line of defense—even before antivirus kicks in.
- On Windows: Go to Settings → Update & Security → Windows Security → Firewall & Network Protection
- On Mac: Use System Settings → Network → Firewall
Local Tip: Most cybercafés in Nairobi run outdated Windows without firewalls—always turn yours ON when switching networks.
Use Backup Software to Protect Critical Files Against The Latest Cyber Threats
Why Backups Matter in Ransomware Cases Against Latest Cyber Threats
Remember that Nairobi-based startup that lost over KES 3 million in 2023? Their data was held hostage by ransomware. They didn’t have offsite or cloud backups, and rebuilding client trust took months.
Actionable Backup Strategy (3–2–1 Rule) When Facing The Latest Cyber Threats:
- 3 copies of your files
- 2 different storage types (external HDD + cloud)
- 1 kept offsite (like Google Drive or OneDrive)
Best Backup Tools for Kenyans Against The Latest Cyber Threats
- Google Drive (15GB free, works seamlessly with Gmail)
- Sync.com (privacy-first, encrypted cloud storage)
- External HDDs like Transcend or WD My Passport (8,500 KES– 11,000K in local shops)
Use Secure Web Browsers and Privacy Extensions In Your Fight Against The Latest Cyber Threats
Best Browsers for Cyber Safety When Facing Latest Cyber threats
- Mozilla Firefox – blocks trackers, supports privacy add-ons
- Brave Browser – blocks ads and fingerprinting by default
- Google Chrome – strong security, but track-heavy unless tweaked
Actionable Setup Tip: Install extensions like uBlock Origin Lite, HTTPS Everywhere, and DuckDuckGo Privacy Essentials for added protection.

Browser Warnings to Never Ignore Against Latest Cyber Threats
- “This site’s security certificate is invalid”
- “Your connection is not private”
- Downloads flagged by your browser or antivirus
Always heed these. Clicking “Proceed Anyway” is like opening your front door to strangers with ski masks.
Turn On Device Encryption & Secure Your Boot Process Against Latest Cyber Threats
We hinted at this earlier—now let’s drill deeper.
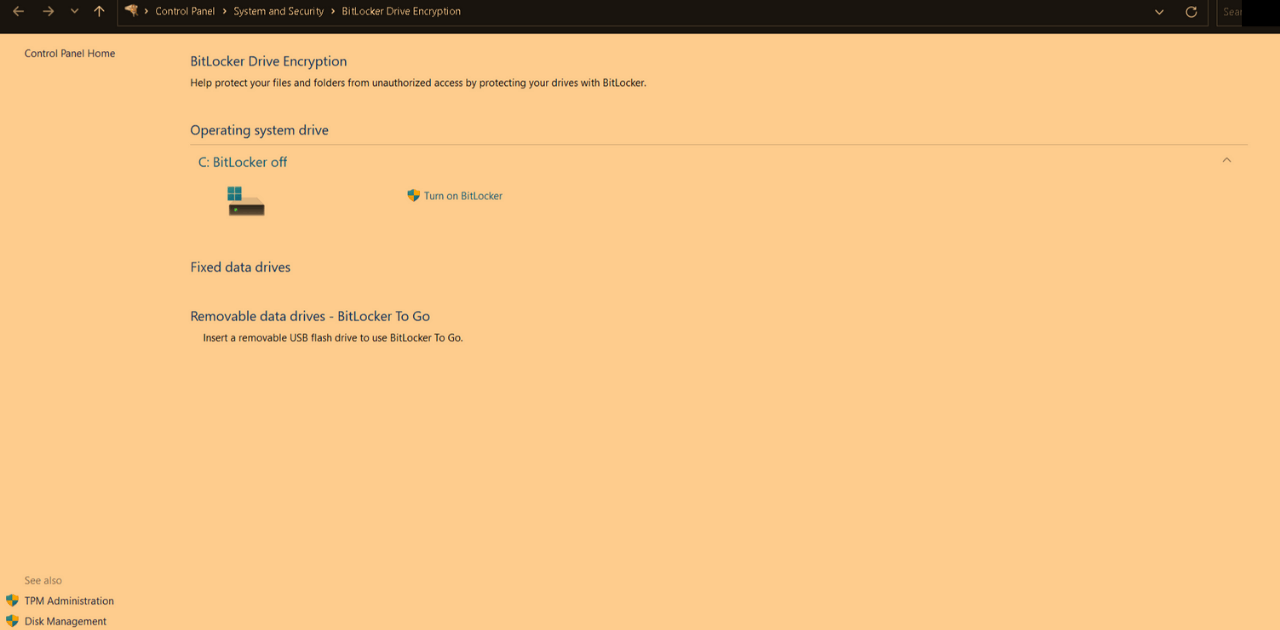
BitLocker for Windows and FileVault for Mac Against Latest Cyber Threats
BitLocker comes pre-installed on Windows Pro/Enterprise.
FileVault is Mac’s full-disk encryption—enabled in Settings → Security.
Even if your laptop is stolen, encryption means the thief sees nothing but gibberish.
Does Encryption Slow Down Performance Against Latest Cyber Threats?
Only slightly, and only on very low-end hardware. The security tradeoff is worth it—especially if you store client data, financial records, or sensitive personal files.
Cyber Hygiene Habits That Actually Work in Kenya Against Latest Cyber Threats
Most cybersecurity breaches don’t happen because of some elite hacker using advanced code. They happen because someone clicked the wrong link, reused the same password, or left their laptop open at Java House while ordering a latte.
Let’s fix that — starting today.
Develop Strong Password Hygiene for All Your Accounts In Your Fight Against Latest Cyber Threats
Never Use the Same Password Twice For Your Security Against Latest Cyber Threats
Most Kenyans use the same password for email, Facebook, eCitizen, and banking. If one gets compromised, they all fall.
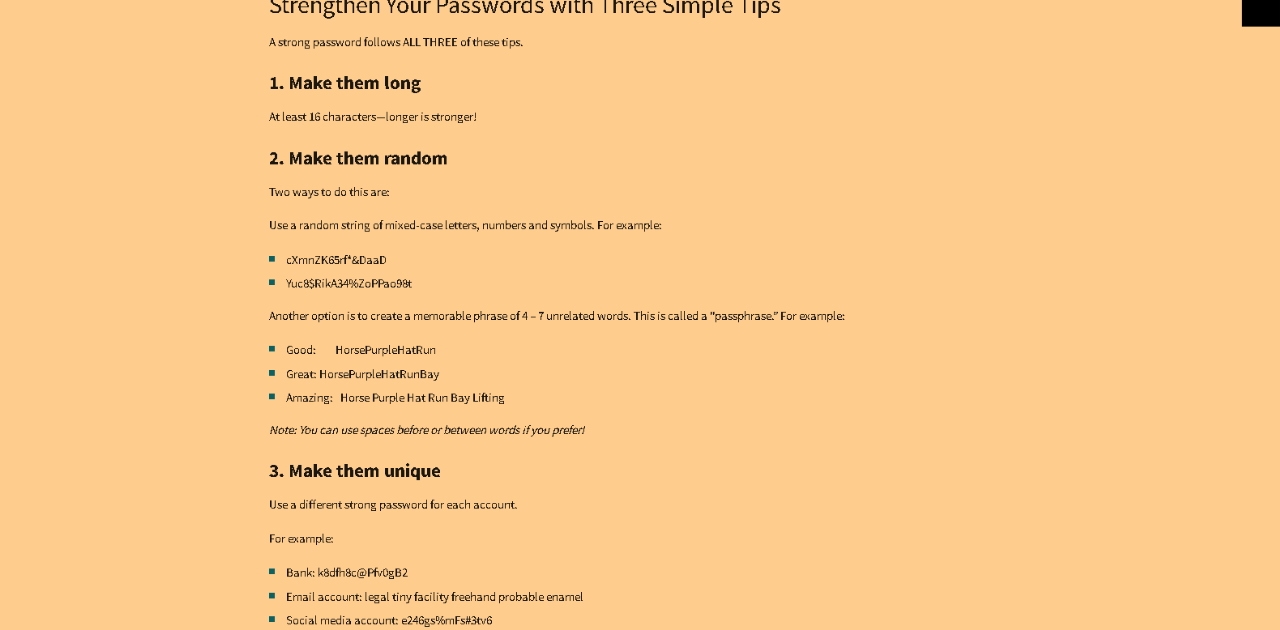
Use this formula to create a strong, memorable password:
[FavoriteFood] + [RandomNumber] + [SpecialChar] + [UniquePlatformCode]
Example: Pilau987!ECIT
Use Password Managers To Protect Your Laptop Against Latest Cyber Threats
You can try the following to protect you from unwanted threats.
- Bitwarden (free and secure)
- 1Password (premium, easier UX)
- Google Password Manager (if you’re deep into the Google ecosystem)
- LastPass (what i personally use)
Local Insight: Avoid writing passwords in notebooks or sticky notes — they’re often stolen during house moves or cybercafé visits.
Watch What You Click – Social Engineering in WhatsApp Groups & Email In Latest Cyber Threats
Kenyan-Specific Scam Trends In The Latest Cyber Threats
- Fake “eCitizen refund” SMSs with links that lead to phishing sites
- WhatsApp links offering free Safaricom bundles (spoiler: malware)
- Emails impersonating KRA agents asking for “document verification”
🚫 If it sounds urgent, scary, or too good to be true — it’s usually a scam.

What to Do Instead To Protect Yourself Against Scams In Latest Cyber Threats
- Verify the sender directly through official channels (like calling KRA or checking the gov.ke site)
- Don’t click any unknown links from WhatsApp, even if it’s forwarded by a trusted contact
- Report suspicious numbers to Communications Authority of Kenya (CAK)
Make Security a Weekly Routine Not a One-Off Event In Latest Cyber Threats
Weekly Cyber Hygiene Checklist for Laptop Users In Latest Cyber Threats
Task Description For Weekly Check Against Cyber Attacks
- Change one critical password Email or banking
- Clear browser cache & cookies Prevents tracking
- Run a full antivirus scan Especially after downloading anything new
- Back up key files Use external HDD or Google Drive
- Review downloads folder Delete suspicious or old files
Bonus: Set a recurring Sunday evening reminder to do this in 15 minutes.
Use Guest Accounts or Admin Controls When Sharing Devices In Latest Cyber Threats
If you share your laptop with staff, friends, or family:
- Create a Guest User account to restrict access
- Turn off file sharing
- Limit app installations using admin settings
Real story: A small business owner in Nakuru gave his laptop to a cousin for Netflix. They installed a free video converter that came with spyware. Sales data leaked a week later.
Signs Your Laptop May Already Be Compromised In Latest Cyber Threats
You don’t always get flashing red warnings when your laptop is under attack. In fact, many cyber threats simmer quietly in the background — stealing your data, spying on your screen, or logging your keystrokes.
Here’s how to catch them early.
Sudden Slowdowns, Crashes, or Unknown Programs Appearing
In Latest Cyber Threats
Not Every Sluggish Laptop Is Just “Old”
If your laptop:
- Takes forever to start
- Shows strange pop-ups
- Crashes during normal use
Has apps you don’t remember installing…it’s likely not just “age.” It could be spyware, crypto miners, or keyloggers eating up your RAM.
Example: A JKUAT student downloaded a free PDF reader from a Telegram channel. It came with a hidden coin miner, slowing their HP Pavilion to a crawl. The battery started overheating — all from malware running in the background.
Unusual Activity on Accounts You’ve Logged into from Your Laptop
Email Notifications You Didn’t Trigger In Latest Cyber Threats
Be alert if you get:
- Security alerts from Gmail, Yahoo, or Facebook
- Login attempts from weird IP addresses (like “Bangladesh” or “Belarus”)
- Password change emails you didn’t request
These may indicate token theft, often pulled by stealthy malware that grabs your cookies or saved login sessions.
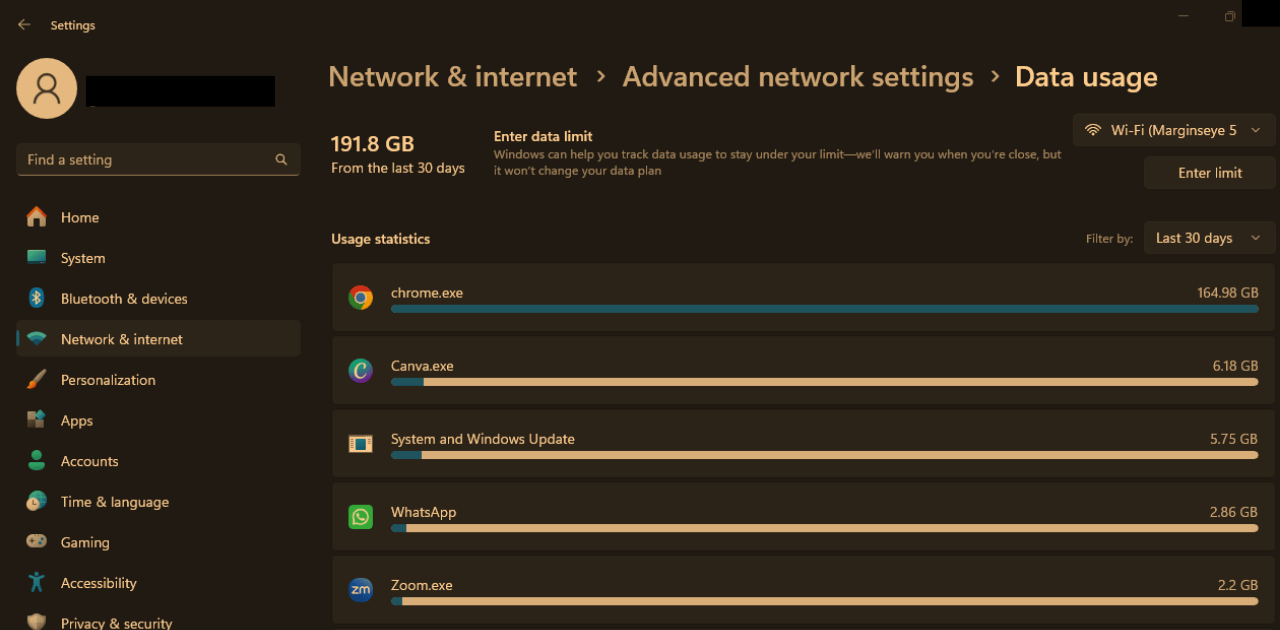
Your Laptop’s Internet/Data Usage Has Spiked Unexpectedly
Monitor Network Activity with Built-In Tools
For Windows:
- Press Ctrl + Shift + Esc → Go to Performance → Network
- Or use Task Manager → App History
For Mac:
Use Activity Monitor → Network Tab
If apps like “Service Host” or “svchost.exe” are using 100+ MBs of data daily, that’s not normal.
Your Antivirus Has Been Disabled or Uninstalling on Its Own
Malware loves to turn off your defenses first. If you see a grayed-out antivirus icon or Windows Defender saying “out of date,” this could mean malware has gained administrator access.
Local Insight: A Nairobi freelancer noticed their ESET antivirus deactivated and blamed system glitches. Turns out, it was a keylogger piggybacking on a cracked version of Adobe Photoshop.
Your Webcam Light Flickers Randomly or Your Mic is Being Accessed
Hackers do access webcams, and it’s not a tinfoil hat theory.
⚠️ If your webcam light turns on when you’re not using Zoom, or if Chrome says “mic in use” — that’s a huge red flag.
What to Do Immediately
- Cover your webcam with tape or a shutter cap
- Revoke microphone and webcam permissions via your browser or OS
- Run a full offline scan (Windows Security → Full Scan → Offline Scan)
How to Respond If You Suspect a Cyber Attack
Don’t panic — act fast and smart.
If you think something’s off, it probably is. Here’s your step-by-step response plan if you suspect your laptop has been hit by malware, phishing, or any form of cyber intrusion.
Disconnect Immediately to Contain the Threat
Unplug from the Internet
- Turn off Wi-Fi and unplug Ethernet cables
- Disable Bluetooth
- If using mobile tethering — disconnect
Why? Most malware needs a live connection to exfiltrate data or connect back to a command center. Disabling access cuts off its oxygen.
Run an Offline Antivirus and Malware Scan
Recommended Tools (That Work in Kenya)
- Windows Defender Offline Scan (built-in, free, effective)
- Malwarebytes Free (download it from a clean device onto a USB)
- Kaspersky Rescue Disk (bootable scan from USB – advanced users)
Pro tip: Always keep an updated rescue scanner on a USB — especially if you’re a freelancer or business owner.
Change All Your Passwords from a Clean Device
Don’t change passwords from the infected laptop. Use your phone or another clean device.
Start with:
- Email (Gmail/Yahoo/Outlook)
- Banking apps (M-Pesa, mobile banking)
- eCitizen
- Social media
Use 2FA (Two-Factor Authentication) wherever possible — it dramatically reduces takeover risks.
Backup Crucial Data (But Not the Malware)
Copy important files (documents, spreadsheets, photos) to an external hard drive or Google Drive
Don’t transfer whole folders or system files — malware often hides there
Tip: Rename your backup folder and only restore data after a full cleanup.
Report the Incident
Where to Report Cybercrime in Kenya
- National KE-CIRT/CC: Kenya’s official cybersecurity response team
Website: https://www.ke-cirt.go.ke
Email: [email protected] - Communications Authority of Kenya (CAK)
Report impersonations, fake messages, scams - Data Protection Office (ODPC)
If client/personal data was exposed
Website: https://www.odpc.go.ke
Include screenshots, email headers, or suspicious links when reporting — it helps others stay safe too.
Reinstall OS or Do a Clean Restore (If Needed)
If malware persists or if it’s a ransomware situation, the safest route is wiping the laptop clean and reinstalling everything fresh.
- Backup first
- Use the original Windows/macOS installer
- Avoid pirated software this time
After reinstall, only restore data you’re confident is clean. Rescan all files before opening.
Real Example
A tech assistant in Nairobi noticed his laptop booting slower and browser tabs freezing. After a scan with Malwarebytes revealed keylogger + spyware, he disconnected Wi-Fi, used a second laptop to change all his login credentials, and reported the incident to KE-CIRT. He later traced the infection to a cracked screen recording tool downloaded from a Telegram group.
Affordable Tools and Software to Keep You Protected in Kenya
Cybersecurity doesn’t have to cost a fortune. Here’s a curated list of affordable (or free) tools to help Kenyan laptop users stay one step ahead of the latest cyber threats.
Free Antivirus Solutions That Actually Work
Windows Defender (Pre-installed)
- Solid for real-time scanning
- Regular cloud-based updates
Pro tip: Schedule Offline Full Scans weekly
Bitdefender Free Edition
- Low-resource usage
- Clean interface
- No annoying popups
Great for freelancers who want set-and-forget protection
Avast One Essentials (Free)
- Web protection
- Email scan
- Wi-Fi Inspector
Bonus: Helps detect if someone’s leeching your home Wi-Fi
Budget-Friendly Paid Antivirus for Kenyan Users
Kaspersky Standard (KES 1,500–2,500/year)
- Top-tier detection rates
- Anti-phishing tools
You can find Local resellers and they have M-Pesa support available to enable you to pay fast
ESET NOD32 (KES 1,800–3,000/year)
- Lightweight and reliable
Great for Kenyan SMEs
Easily bought via resellers like Saruk or Jumia
Must-Have Backup Tools for Laptops
Google Drive (15GB Free) Sync files automatically
Version history helps roll back infected files
AOMEI Backupper Standard (Free for Windows)
- Full system backup
- Easy to restore if malware hits hard
- Store backups on external drives
Tip: For sensitive client work, consider paid cloud options like pCloud or Sync.com, which offer better encryption.
Browser Extensions to Prevent Online Attacks
uBlock Origin (Adblocker + Anti-Malware)
- Blocks ads, trackers, and known malicious domains
- Light and fast
- Available on Chrome and Firefox
HTTPS Everywhere (EFF)
- Forces secure connections
- Reduces risk of man-in-the-middle attacks (especially on public Wi-Fi)
Privacy Badger
- Learns to block trackers automatically
- Created by Electronic Frontier Foundation
- Useful when browsing high-risk websites (like forums or cracked software sites)
Password Managers (No More “123456” or “password@2023”)
Bitwarden (Free & Open Source)
- Stores all passwords in one encrypted vault
- Auto-fills logins
- Works on desktop, phone, and browser
KeePassXC (Offline Password Manager)
- Ideal for users wary of cloud syncing
- Passwords are stored locally and securely
Bonus: Pair with 2FA apps like Google Authenticator or Authy for ironclad logins.
Real-World Use Case: Nairobi-Based NGO
A local NGO working in education switched to Bitwarden for password management and ESET NOD32 for endpoint protection. They trained their team to use uBlock Origin, kept backups on Google Drive, and avoided public Wi-Fi without a VPN. Their setup costs them less than KES 5,000/year — and they’ve had zero breaches in 2 years.
Best Practices for Everyday Cyber Hygiene
These aren’t just “good-to-do” — they’re must-do habits to keep your laptop, data, and privacy locked tight. We’ll break them down into:
- Daily habits
- Weekly routines
- Monthly must-dos
Daily Cybersecurity Habits (5 Minutes or Less)
Think Before You Click
- If it smells scammy, it probably is
- Hover over links before clicking — especially on emails or SMS
- Don’t open random attachments — even if it’s “from Safaricom”
Real Example: A student in Eldoret clicked a “KRA Refund” PDF, which silently installed spyware. His laptop started emailing spam automatically. Always verify and scan before opening.
Use Password Managers — Not Sticky Notes
- Store logins in Bitwarden or KeePassXC
- Never reuse passwords
- Add 2FA to M-Pesa, Gmail, social accounts
Avoid Public Wi-Fi Without a VPN
- If you’re in Java House or Sarit Centre, assume someone is sniffing traffic
- Use your phone’s hotspot instead — or a VPN like ProtonVPN (Free Plan)
Weekly Cyber Hygiene Routines
Run Antivirus & Malware Scans
- Schedule Windows Defender Offline Scans or use Malwarebytes
- Check for new or unusual startup programs
Backup Important Files
- Set Google Drive or OneDrive to auto-sync
Alternatively, backup to an external hard drive every Friday
Update All Apps and OS
Enable auto-updates for your OS and apps
Prioritize updates for:
- Browser
- Antivirus
- Messaging apps (WhatsApp, Telegram)
Why? Most hacks exploit old vulnerabilities — especially in pirated or outdated software.
Monthly Cyber Maintenance
- Check Your Digital Footprint
- Google your name/email — see what’s publicly visible
Revoke access from sketchy third-party apps (check Google Account > Security > Third-Party Apps)
Clean Your Downloads and Trash
- Malware often hides in unzipped folders and .exe files
- Empty trash bins regularly
Review Privacy Settings on Social Media
- Limit who can see your info/posts
- Turn off location sharing unless needed
Audit app permissions (e.g., does Facebook still have access to your mic?)
Pro Habit for Freelancers & Remote Workers
- Set a Cyber Check-In Day at the end of every month:
- Review your login logs (Gmail, Dropbox, Facebook)
- Check if any logins were from unknown devices or IPs
Change passwords if suspicious
Real-World Insight: Kenyan Freelance Graphic Designer
“I used to ignore Windows updates until one day my laptop got locked by ransomware. Now, I run a quick scan every Sunday night, back up client files to Drive, and never connect to free Wi-Fi unless I’m using ProtonVPN.”
Final Thoughts: Staying One Step Ahead of the Latest Cyber Threats
Going online in Kenya in 2025 is no longer optional — from transacting on eCitizen to applying for jobs on LinkedIn, your laptop holds your life. and so, the question is no longer “Will cyber threats reach me?” It’s “How prepared you will I be when they do?”
Cybercrime in Kenya is rising fast — from SIM swaps to KRA impersonators and ransomware attacks targeting small businesses.
Most users don’t take cybersecurity seriously until it’s too late — data is gone, accounts are hijacked, or money disappears.
Imagine waking up to find your laptop locked, your client files gone, and a demand for $500 in crypto. Or having your Gmail account hacked — with access to your M-Pesa, Facebook, and bank alerts.
For many Nairobi startups and freelancers, this isn’t hypothetical — it’s already happened.
You don’t need to be an IT expert or break the bank to get prepared. With the right habits, tools, and awareness, you can stay two steps ahead of even the latest cyber threats.
And now you have everything you need to start — curated for real users, living and working in Kenya.
REMEMBER this Cyber Hygiene Checklist (Save & Share)
- Use a password manager like Bitwarden
- Activate 2FA on Gmail, eCitizen, Facebook
- Run antivirus scans weekly (Windows Defender or Bitdefender)
- Back up important files (Google Drive or External Drive)
- Avoid public Wi-Fi or use ProtonVPN
- Don’t click on suspicious SMS/WhatsApp links
- Update your apps and OS regularly
- Review social media privacy monthly
- Scan downloads before opening
- Keep your browser extensions clean
Stay Updated and Subscribe to updates from trusted cyber sources like:
Join conversations on:
- r/Kenya on Reddit (for local cyber scam reports)
- Facebook groups like “Phones & Laptops Group Kenya”
- TechTwitter Kenya for real-time threats and solutions
Finally , the goal isn’t paranoia. It’s empowerment. You deserve to create, work, and explore freely — without fear of being digitally ambushed. The web is wild. Be smarter. Be safer. And be one step ahead.
Want to read more articles, read more on the MarginseyeKE Blog